Hash function, stretching salt
Hello. Hello. This is Nishimura. We are very busy at the end of the fiscal year, but we are doing well.
I don't know the password.
I have a question to the support team of learningBOX, I forgot my password, can you tell me? Can you tell me my password? From the customer's point of view, the service operator should know the password, right? But in fact, we have no way of knowing what the password is.
Passwords are hashed.
In learningBOX, passwords are stored in hashed form. Hashing is to perform some operation on the original value to create a value that does not know what the original value is, although it knows the characteristics of the original value. For example, let's consider the hash function "find the sum of each digit for an integer". It is easy to find the right from the left, but it is not possible to find the left from the right, right? We can do this with the hash functionunidirectionalityIt is called
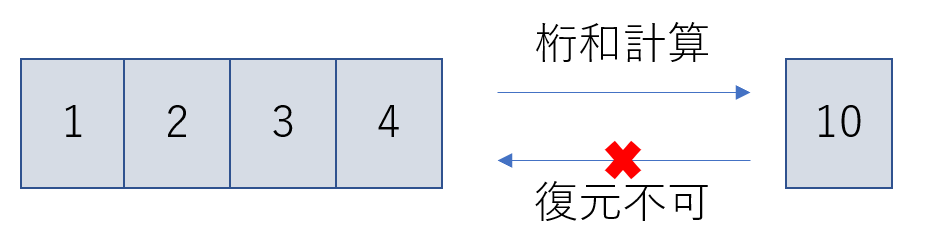
In the above example, it is not possible to guess the left value from the right value. However, the left value is not secure as a password authentication system because the right value can be easily obtained to be the same as the left value. How difficult it is to guess the right value is called collision resistance or collision security, and it is important to use an appropriate hash function.
Stretching to buy time.
Brute force attack. In a so-called brute force attack, if every possible password is tried, any password can be broken. Stretching the time for this brute force attack is a technique called stretching. Modern CPUs are fast, and GPUs are much, much faster. The hash function that can be executed with 100,000 calculations can be executed 100 million times per second. In other words, an eight-digit password can be cracked in one second. That's not good. If you use alphabet and numbers, it might take a day, but it can be broken in a day. It's bad. That's where stretching comes in. Stretching is a way to buy time by repeatedly passing a hash function. 1024 times will increase the time from 1 day to 1024 days. It's safe.
Salt to safety.
Even if it takes 1024 days, that's on a gaming PC. If you have a budget of 10 billion yen, you can break it. It's a piece of cake. If you have a budget of 10 billion yen, you can make a magic reverse dictionary called Rainbow Table, which can find the hash value after stretching for all possible passwords up to 10 digits. (*This is not the exact amount.) To counter this, you can season your passwords with salt. In this way, you can prevent the reverse lookup attack by Rainbow Table. Of course, it is possible to break the password if 10 billion yen is poured into the game to break the password, but there is a balance.
Online and Offline Attacks
The story of Stretch and Salt was actually about an offline attack. The offline attack is a method to estimate the password by brute force on the PC against the hashed value leaked to the outside. This is not an incident, but an accident. It is not an incident, but an accident. It's a serious situation. In order to prevent such a situation from happening, we maintain development processes, enforce coding rules, conduct code reviews, and conduct vulnerability assessments. On the other hand, "online attacks" are easy to execute. An online attack is an attempt to log in by entering your ID and password at the login screen. Anyone can do it.
Prevent online attacks: limit the number of times
If you enter your password incorrectly N times, you can lock your login. Starting with learningBOX 2.10.x, you can set a limit on the number of incorrect password entries.
Preventing Online Attacks: Two-Factor Authentication
learningBOX can notify you of an additional authentication key via email if your ID and password are entered correctly. By using this feature, unauthorized login is not possible unless the login credentials are broken in the mailbox to which the authentication key is sent.
Preventing online attacks: IP address restriction
When you sign up for a dedicated learningBOX server, you can restrict the IP from which you can connect. In other words, you can restrict the connection only from your company.
Finally.
Security technology is constantly evolving. It is important not to be satisfied with just learning once, but to always continue to incorporate new knowledge. It is also important to keep learning new knowledge.Information Security Management Examinationand National Examination for Information Processing Security AdvisorsYou can acquire overhead knowledge efficiently by obtaining official qualifications such as Although I am also non-registered, I have taken and passed the Information Processing Safety Assurance Support Specialist exam. ✌
- How to throw an HTTP request through a Proxy in PHP
- What you need to know about new employee training and how to maintain motivation
Comment ( 0 )
Trackbacks are closed.




No comments yet.