Data Breaches Threats and Countermeasures

In recent years, many companies have come to realize that the danger of information leaks lurks close at hand. This is because cybercrime techniques are becoming more sophisticated every year and any company can be targeted.
There are also cases where information leaks occur due to human error within the company, against a background of insufficient employee training.
This section describes the risks that such information leaks pose to companies, measures to prevent them from occurring, and the response flow in the event of an outbreak. Let's review your company's information leakage countermeasures.
List of risks posed by information leaks

In recent years, more robust measures have become necessary to reduce the risk of information leaks. There have been many cases of serious information leaks that could not be handled by conventional security measures alone.
This is due to the spread of telework due to the spread of the new coronavirus infection and the proliferation of mobile devices, including smartphones and tablets for business use.
According to a survey by the IPA (Information-technology Promotion Agency, Japan), "attacks targeting telework and other new-normal work styles" have been newly ranked among information security threats since 2021. First, here is a list of risks to be aware of.
Ten Major Threats to Information Security 2021" (Information-technology Promotion Agency, Japan)
<List of risks posed by information leaks
| class | risk | Examples of actual events |
|---|---|---|
| primary risk | Become a victim of identity theft and fraudulent use | -Unauthorized use of customer credit cards - Corporate SNS account hijacking - Proliferation of corporate spoofing emails |
| Damages and criminal penalties | - Penalty of up to one year in prison or a fine of up to 500,000 yen for the perpetrator. - Payment of 10,000 yen to all victims - Distribution of 500 yen golden tickets to all victims |
|
| Web site is tampered with | - Unintended advertisements are displayed - Automatic access to another site - Infecting viewers with malware |
|
| secondary risk | Social credibility is diminished. | - Transactions of important customers are discontinued. - Smaller market share - Negative publicity is spread on social networking sites. |
| Leads to employee anxiety and distrust | - More retirements. - The atmosphere in the workplace becomes worse. |
Become a victim of identity theft and fraudulent use
Spoofing is the act of a third party pretending to be someone else on the Internet, leading to the misuse of personal information such as IDs, passwords, and e-mail addresses.
There is concern that emails impersonating the company may be spread, customer credit cards may be fraudulently used, and company social networking accounts may be hijacked.
Damages and criminal penalties
If a leak of personal information is discovered, you may be subject to a government order to take action and a fine. the revision of the Personal Information Protection Law, which came into effect in April 2022, has strengthened the order to take action and the fine.
Violation of a measure order is punishable by imprisonment for up to one year or a fine of up to 1,000,000 yen.
In some cases, information leaks may also result in civil liability for damages. This is because information leaks constitute a tort that illegally infringes on the rights and interests of others.
Furthermore, in some cases, apart from damages, companies have paid apologies in the form of golden certificates, electronic money, or points.
2020 Revised Personal Information Protection Law" (Ministry of Internal Affairs and Communications)
Web site is tampered with
There is a risk that a malicious third party will gain unauthorized access to a website by targeting its vulnerabilities and falsify its content without its knowledge.
In addition to displaying advertisements that have nothing to do with the company's business, there are also methods that direct users to fake sites or infect them with malware, so caution is required.
Decrease social credibility
Information leaks can damage the trust of business partners and customers and damage social credibility and brand image, as well as cause rumors on social networking sites and a drop in stock prices.
If an accident leads to the inevitable suspension of business activities or service operations, it could result in significant losses.
Leads to employee anxiety and distrust
Information leaks can also have a significant impact on the company. Employees may become anxious and distrustful of the company, and their motivation for work may easily decline.
It is also important to note that it is easy for employees to become overworked and stressed out from dealing with outside parties after an accident, which can lead to an increase in retirements.
Back to ContentsMajor causes of information leaks and examples of measures to reduce risk

What are the main causes of corporate information leaks? Take measures for each cause to ensure thorough information management in your company.
Main causes of information leaks
The causes of information leaks can be broadly classified into three main categories: leaks due to internal human error, intentional leaks from within, and leaks due to external attacks. To prevent information leaks, it is necessary to implement measures from multiple angles depending on the cause.
<Examples>
| class | main causes | source | factors | |
|---|---|---|---|---|
| internal | human error | - lost or misplaced recording media - careless conversation in public places or social networking sites - mishandling of emails and systems |
- employees - retirees - outsourcing employees - part-time employees - contractors, etc. |
- carelessness - lack of knowledge |
| intentional | - unauthorized transmission of data - manipulation |
- economic reasons - dissatisfaction with the organization, etc. |
||
| external | Malicious Attacks | - cyber attack - malware infection - eavesdropping and theft |
- attackers - threat actors - hackers, etc. |
|
Examples of countermeasures against information leaks [by cause
Human errors such as "lost or misplaced," "mishandling," "mismanagement," and "theft" account for more than 60% of information leaks. These are figures published in a 2018 survey by the Japan Network Security Association.
2018 Survey Report on Information Security Incidents, Japan Network Security Association.
From these results, it can be said that there are relatively many information leaks that can be avoided depending on employees' knowledge and awareness of security information. Regular training and the formulation of guidelines and rules are effective measures.
The following table summarizes effective information security measures for each cause of human error. Please take a look at it for reference.
<Examples of causes of information leaks due to human error and countermeasures
| cause | Examples of countermeasures |
|---|---|
| mismanagement | - Do not connect private computers to the company network - Always shred paper documents. - Use different email addresses for business and personal use - Not leaving a business computer without locking it |
| misoperation | - Implement a system to prevent misdirected e-mailsImplement a system to prevent misdirected e-mails - Encrypt transmitted data |
| Lost or misplaced Eavesdropping and theft |
- Do not place luggage on train screens. - Do not take company information home - Do not use USB memory sticks or other storage media that can be carried around - Do not send out information about your work on social networking sites - Do not talk about work in public places such as elevators or taverns |
Response flow to limit risk in the event of an information leak

If an information leakage incident occurs at your company, use the following flow to respond promptly. Finally, here is the response flow that should be confirmed in case of an emergency.
Step 1: Confirmation and Prompt Report
If any signs of an information leakage or the impact of a leakage after its occurrence are confirmed, immediately report the leakage to the person in charge. First, the person in charge will establish the internal system and the policy and details of the primary response.
In doing so, please be careful not to inadvertently manipulate the equipment used so as not to erase evidence that may provide clues to the cause of the problem. For example, do not delete emails or files related to the situation.
Step 2: Prevent Secondary Damage
Next, emergency measures will be taken to prevent the information leak from spreading and causing secondary damage. In some cases, measures such as temporary suspension of services may be considered.
In the case of a personal information breach, it is also necessary to contact the affected person and ask him/her to change his/her password or stop using the service.
Step 3: Conduct a Reasonable Investigation
After conducting a fact-finding investigation and determining the cause of the information leak, accurate information will be made public. The important thing is to release information that is well-founded and highly reliable.
Please take care to avoid sending out information that may cause confusion, such as ambiguous information or speculation.
Step 4: Announcement to the Relevant Authorities
In order for companies to fulfill their accountability for information leakage incidents, they are required to report to the relevant authorities and make public announcements. In addition to notifying suppliers and customers, notification to regulatory authorities, the police, and the Information-technology Promotion Agency (IPA) is also required. The timing of public announcements should be established after considering whether there is any risk of damage escalation.
Step 5: Take Prevent Measures
Once the initial response is completed and business activities and services are restored, we work on measures to prevent recurrence. We identify the issues based on the cause of the information leak and implement countermeasures, as well as compensate damages to the victims and discipline employees.
Depending on the content of the public announcement of preventive measures, there is a risk that a third party may learn of the vulnerability, so the scope of the public announcement should be carefully considered.
Back to ContentsTo prepare for the risk of information leaks
We have introduced countermeasures to prepare for the risk of information leaks and a response flow to minimize damage. The majority of information leaks are caused by human error on the part of employees.
Improving internal information security training is believed to reduce risk. Be prepared for any eventuality and focus on employee education.
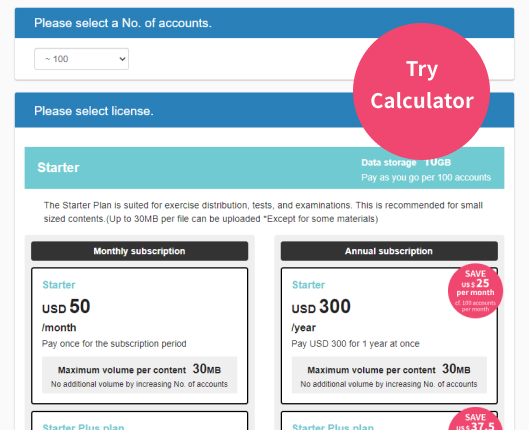
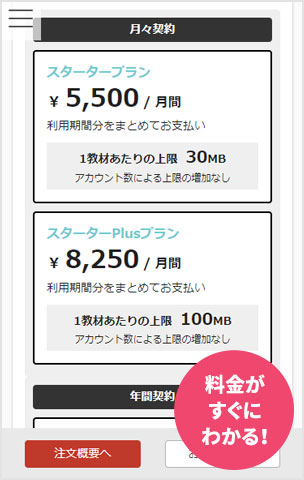
Please use the information security training contents of "learningBOX ON" to familiarize yourself with information security within your company.
learningBOX is a cloud-based elearning platform
and you can easily build training courses online.
Created content will be delivered to employees and you can track their learning progress.
There will be something you can do to improve your work environment.
▼You may also like:
Back to Contents


-
Discover rich featuresService Guide
-
Feel free to contact usGet in Touch
-
Try our Free PlanTry Free Plan