Security Training Using e-Learning to Prevent Information Leakage
A ministry that prevents information leaks
"Security training using e-learning."
I'm 👓 Kinoshita, CS implementation support manager. It's been a while since I've posted a blog article, and there are only a few days left in 2019. It's been a hectic year with the change of the new year's date, hasn't it?
2049 was a year of great change for our company.Moved to a new office and participated in exhibitions in Tokyo and Osaka.There were many big events such as the following, and we thank you very much for your support on those occasions. I would like to take this opportunity to thank you again. So, without further ado, let's get to this issue's article!
"Does your company have the right security knowledge, measures and training?In this article."We're introducing a security training program that uses e-learning to protect your company's customer information from leaks and precautions in handling customer information!We look forward to working with you on this paper.
Content
- 1. compensation for damages caused by leakage of personal information
- 2. the importance of security training
- 3. demand and expectations for e-learning
- 4. create a security training program using the learningBOX
- 5. Summary
Compensation for damages caused by personal information leaks
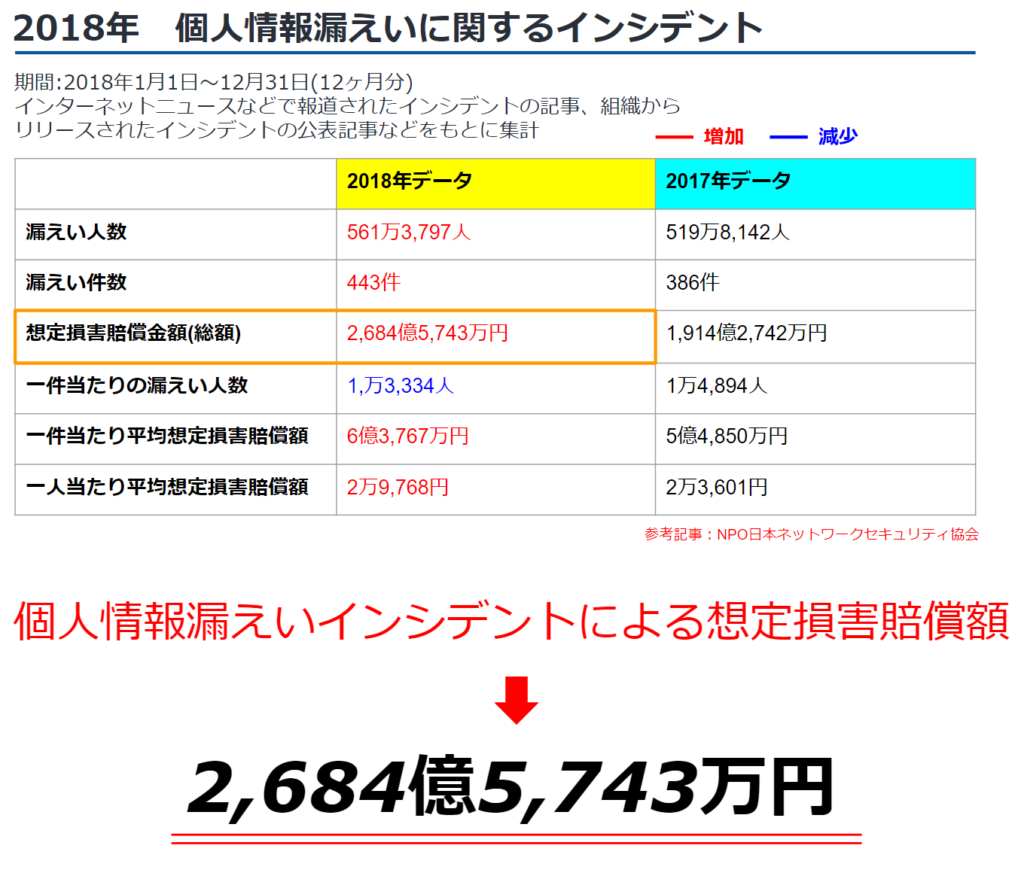
This one occurred in the year 2018.This is the estimated amount of damages caused by a personal information leakage incident.In terms of the number of people exposed per information leakage incident, the Information and Communication Industry occupies the top position (No. 1, 1,712,580).
(Source.Japan Network Security Association
The Importance of Security Training
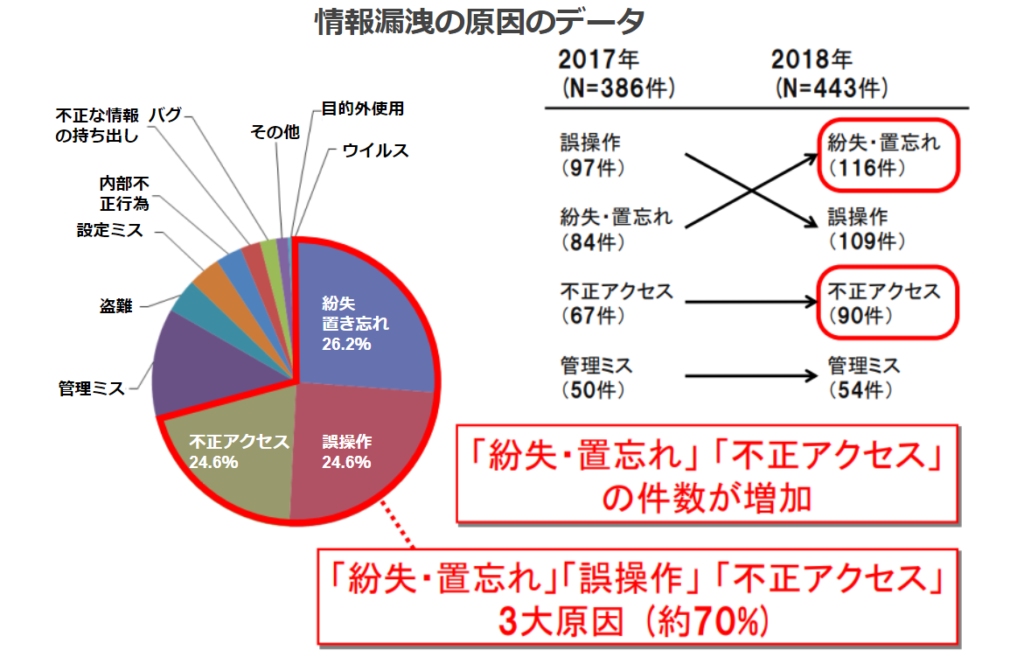
by cause
1st place Lost and found 26.2%
2nd place: Misoperation 24.6%
3rd place: Unauthorized access 20.3%
The three major causes are "lost or misplaced," "mishandling," and "unauthorized access," accounting for about 701 TP1T of the total. As can be seen from the causes, the most common causes are omission of confirmation and lack of security awareness.human erroris related to the cause of the problem, and it is essential to improve the security awareness of all employees, including company executives. (Source.Japan Network Security Association
The effects of information leaks cause immeasurable damage to customers and business partner companies. Economic loss, loss of trust in the company, penalties, penalties, etc. ... It is terrible even just to think about it.
Demand and Expectations for e-Learning Learning
Training and learning through e-learning isEducation Big Data, EdTech, Work Style Reform, Next Generation Group Training, and Advanced EducationIt is expected to be one of the forms of learning. It is expected to be a form of learning, and the number of companies introducing it is increasing every year. Among them, more and more companies are focusing on training and education for internal use, such as compliance, information security, and corporate training.
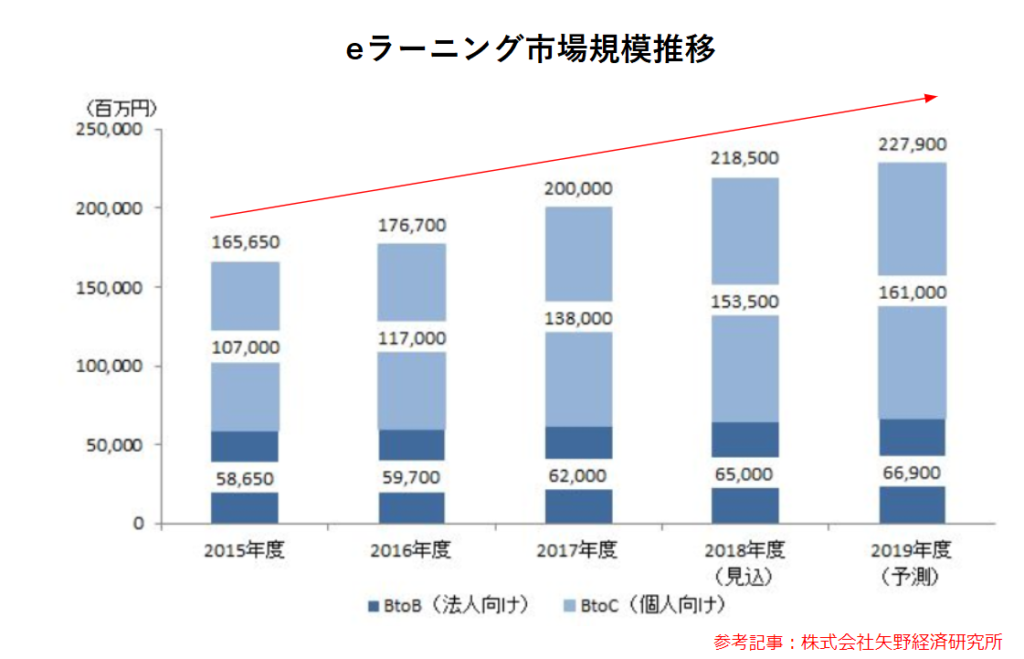
Benefits of e-learning

E-learning is very convenient because it allows individuals to study as needed and repeat what they do not understand. The greatest advantage of e-learning is that it is easy to prepare, review and relearn at the timing you want to learn. By improving each person's business skills, it helps employees, the company, and the entire company to grow and raise the bar, which directly leads to improved business efficiency.
Conducting security training using a learningBOX
This is how Tatsuno Information Systems does it."Security Trainingto our employees. Our learningBOX allows you to easily create and implement security training. This time, we will introduce the security training using the contents provided by IPA (Information-technology Promotion Agency, Japan) for free.
IPA (Information-technology Promotion Agency, Japan)
The National Institute of Information and Communications Technology (NICT) is a policy implementation organization that plays a role in IT policies to realize a "reliable IT society" by ensuring the safety and reliability of the increasingly complex and voluminous information society systems, and develops measures for information security, software reliability, and IT human resource development. (Citation: Japanese only)IPA (Information-technology Promotion Agency, Japan)
Security Training Flow
Click here for security training using learningBOX. Please check the video
With learningBOX you can take security training as a course study. By making it a course learning, you can issue a certificate only to those who have reached certain learning steps and passing scores.
We also recommend these features and settings
Have each group or department receive training.
You can import all the results of learners by CSV.
It is also possible to limit the number of lessons.
The learner's performance data is automatically scored.
How to set up and use the learningBOXHow to use the learningBOX pageYou can find more information on this in the
Summary
In security training, it is important to raise the awareness of all employees. Simply handing out thick materials or communicating a token policy will not improve employee awareness.
It is important to have a system that complies with security, and one such system is e-learning, which allows you to analyze, quantify, and evaluate the level of understanding of your learners. We hope that our e-learning system (learningBOX) will be useful for your company's security measures. Thank you very much for taking the time to read this article.
Comment ( 0 )
Trackbacks are closed.


No comments yet.